Tracking Vulnerability State Over Time
.png)
Most security scanners are stateless. They give you a point-in-time reference / view of the current vulnerabilities, but they don’t track how those findings change over time. At Leen, we’ve built an internal system that captures the full lifecycle of vulnerabilities - not just what exists today, but what was there yesterday, what changed, and why.
The Problem
While scanners track states like first seen, resolved, and reopened, they don't typically store full historical state transitions across scans in a structured way. This makes it difficult to:
- See complete state change history over time
- Analyze remediation velocity accurately
- Understand recurring patterns of reopening or state flapping
Most scanners leave this tracking to the end user or external systems.
How Leen Does It
Leen ingests raw data from multiple vendor APIs (eg: Wiz, CrowdStrike, Snyk etc). From there:
- We normalize: All data is mapped into a common schema regardless of the source.
- We store snapshots: Each ingestion cycle creates a versioned snapshot in S3. Nothing is overwritten.
- We track state:
- We compare new snapshots against previous ones.
- Each finding has a tracked state:
open,closed,reopened,ignored,deleted
- We cache findings: This allows us to persist long-term visibility even if vendors remove or redact issues.
This is implemented through a simple ETL pipeline with different logic built into the transform phase. We also maintain an internal changelog for each normalized vulnerability.
Example
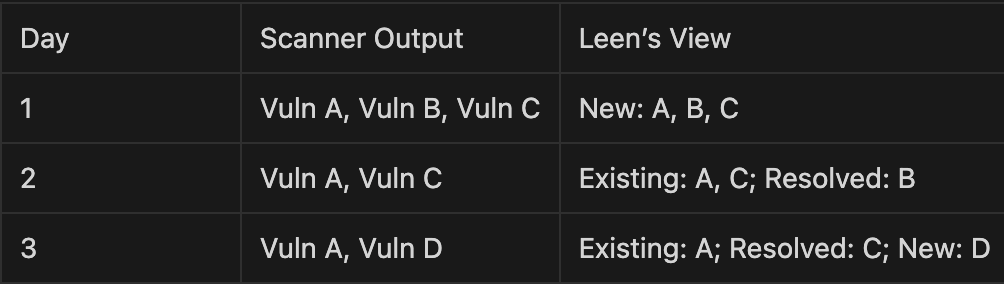
Most scanners only show what’s on Day 3. Leen shows what’s new, what’s resolved, and what’s persisted.
Why This Matters
With Leen, you can:
- Show the full history of a vuln across scans
- Identify regressions (eg: reopened vulns)
- Power SLAs and compliance reporting (eg: time-to-remediate)
- Reduce noise by alerting only on state changes (not repeated findings)
Why Scanners Don’t Do This
- They are not built for historical storage
- They are designed for detection, not aggregation
- They don’t maintain state or history between scans
- They rely on the user to handle vuln life-cycle management
Vulnerability data isn’t static, but most tools treat it that way. By persisting state transitions across scans, Leen allows security teams to work with complete context, not just current snapshots. This enables better prioritization, cleaner remediation workflows, and accurate historical reporting – all without replacing your existing scanners. It’s a foundational layer that turns vulnerability management into an actionable, state-aware system.



.png)
.png)

.png)